Definition - Relationships between certain authorizations in disparate systems or shared file areas (SFAs) can be established so that altering an account's authorizations for one of those systems or SFAs can trigger additional authorization changes other systems or SFAs. This concept is called piggybacked authorizations.
Triggers - Piggybacked authorizations can be defined to occur whenever an authorization is added, removed, or both. When any authorization within a piggyback is changed, a window appears to the keygiver optionally allowing other authorizations to also change.
Keygiver status - As with all authorizations, the keygiver must be a keygiver for all systems/SFAs in the piggyback in order to make the authorization changes. Any system or SFA for which the keygiver does not have keygiver privileges will be shown in red and will not be issued/removed if the keygiver clicks the "Submit" button.
Limitations - Currently, piggybacked authorizations cannot be defined to include both systems and SFAs. Authorizations included within a piggyback limited to systems or SFAs; that is, a system change cannot be piggybacked to an SFA change, and an SFA change cannot be piggybacked to a system change.
Existing piggybacks - To view all the defined piggyback combinations, see the Piggybacked Authorizations Report.
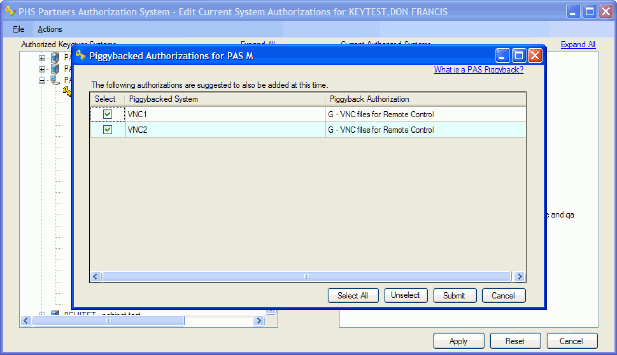
Example - The PAS "M" authorization has been set up to be piggybacked with the VNC1 "G" and the VNC2 "G" authorizations. When a keygiver selects and adds the PAS "M" authorization, the following window appears:

When the keygiver clicks the Submit button, all checked piggybacked authorizations are issued as shown (changes in blue text):
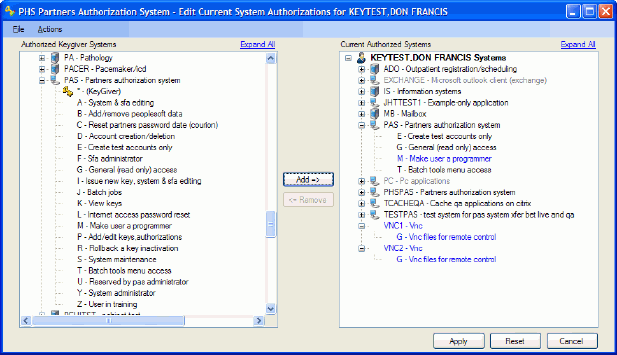
Alternately, when the keygiver clicks the Cancel button, only the original authorization (PAS "M") is issued as shown (change in blue text: